Banning arbitrary people in Rainbow Six Siege
7.2.2025 | siege-banning-exploit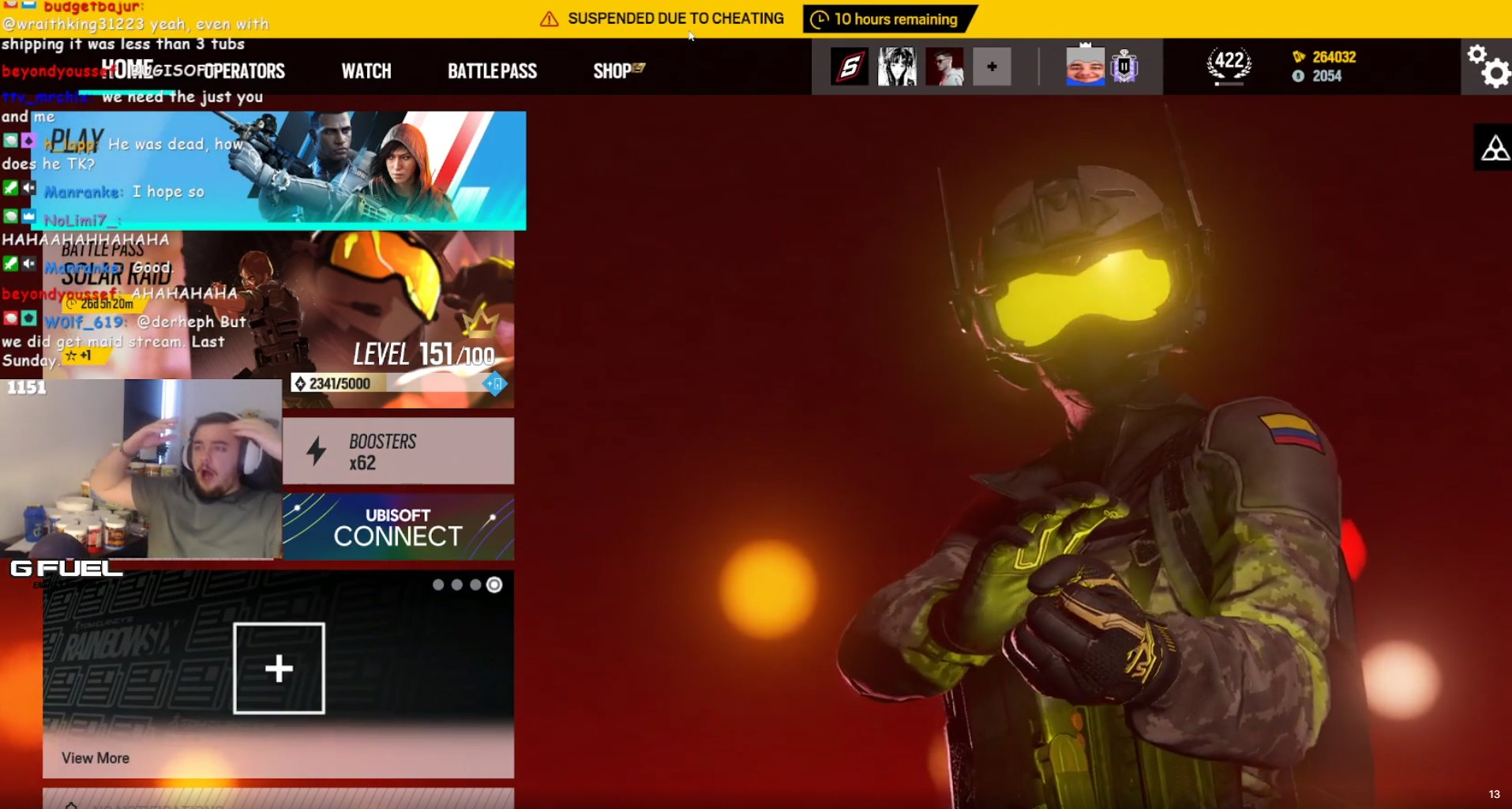
About 2 years ago, I found an exploit within Ubisoft’s API that basically allowed me to ban other players from playing Rainbow Six Siege. Let me explain:
Rainbow Six Siege?
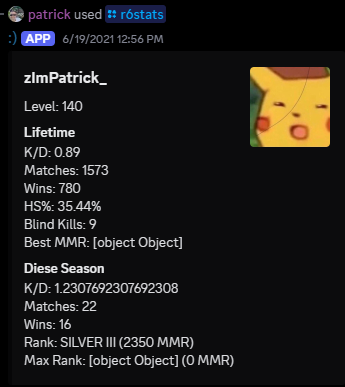
Tom Clancy’s Rainbow Six Siege is a tactical 5v5 hero-shooter, which is basically the only live service game that kept Ubisoft afloat for the last few years. My friends and I enjoyed it a lot back then and, me being the nerd I am, wanted a quick way to check the statistics of my enemies and their most-played operators without needing to go to the stats tracking website everyone used.
This website has a developer program - however that doesn’t include access to Rainbow Six Siege, so getting an API key and just calling that won’t work.
They also had an overwolf extension that allowed you to view your enemies’ statistics ingame, however I did not feel like trusting Overwolf with my computer. It might be fun looking into Overwolf sometime and checking how they get game info without triggering an anti-cheat. So, like the idiot I am, I downloaded Overwolf in a virtual machine and installed the extension. Overwolf extensions are basically just webapps, so you can just look at the javascript files and quickly figure out what endpoint they’re calling to get statistics. One simple GET request implemented into a monolith of a discord bot later, I got it working okay-ish.
But what about Ubisoft’s API?
Again, the discord bot simply sent a GET request to https://r6.tracker.network/api/v0/overwolf/player?name=InsertUsernameHere, but what about trying to use Ubisoft’s “internal” API?
NOTE: My interpretation of “internal” APIs are APIs, that are not meant to be called by other external programs, like a stats tracker. It’s probably not the right definition, but I’m going with it here.
Coming from Fortnite, where basically every API call is documented, with many open source “private servers” (aka: reimplementations of the backend) and a public SSL pinning bypass existing, it was hard to find where to start, as not many people published information about Ubisoft’s backend at the time, the only readily available resource, or at least the one I found, was a GitHub repository called Rainbow-Six-Siege-Player-Stats-API by Seems2Legit written in PHP. (I, kind of, despise PHP, btw.)
So, I got to work testing these endpoints by trying them in an API client (in my case, Insomnia as it wasn’t that bad back then) and later implemented these into the discord bot. Everything worked fine… but because I was a curious person, I decided to investigate further to see if I could gather any more data. I found a few more endpoints with interesting data in an, still open, GitHub issue in the same repository. SwiftCODA’s comment containing many other endpoints helped me onto the right track. I’m still a bit confused on how they got this data, as all my attempts intercepting HTTP requests didn’t work back then.
I decided to write a small script monitoring, what I thought to be, the 5 most important endpoints, which boiled down to checking if there was some change in these endpoints, then sending a diff into a discord channel. I decided to use a discord channel because I already had experience with webhooks and it was an effective alerting method for me at the time. To this day, it has tracked more than 300 thousand changes.
Requests
Every request to their API has to contain an Ubi-AppId correlating to some application. Because they use the same API across their entire fleet of games, applications and websites, you can easily find one of these by simply opening the developer tools on https://ubisoft.com.
Some endpoints check for a specific application id, so you couldn’t just use the same one for every endpoint. This will come in handy later.
As far as I understand it, games are separated by so-called spaces, each space has its own set of configurations, offers, items, etc. One of the more important endpoints of these so-called spaces is the /parameters endpoint, as it contains configuration options for Ubisoft’s SDK and for the game itself.
{
"parameters": {
"us-sdkClientNotificationsGame": {
"fields": {
"BAN_ALERT": true,
"UPDATED_PENALTIES": true,
"LIVE_ESPORTS_EVENT": true,
"PUBLIC_ANNOUNCEMENT": true
},
"relatedPopulation": null
},
"us-sdkClientUrls": {
"fields": {
"news": "{baseurl_aws}/{version}/profiles/me/news",
"tLog": "https://tglog.datamore.qq.com/{appId}/report/",
"users": "{baseurl_aws}/{version}/users",
"events": "{baseurl_aws}/{version}/profiles/{profileId}/events",
// ...and many more
"connections": "{baseurl_aws}/{version}/profiles/{profileId}/connections",
},
"relatedPopulation": null
},
"r6-publicConfigs": {},
// if I included everything, there would be about 3451 lines here.
}
}Connections?
As I said before, I started toying around with most of the endpoints listed here, however I seem to have forgotten about the /connections endpoint:
{
"connections": [
{
// this is not all of the needed data..
"connectionId": "0a84da06-3fca-4777-b257-077ffb38d661",
"applicationId": "20adeb9c-6dad-404e-af1e-b12b4594e86e",
"contactUrl": "https://public-im-ubiservices.ubi.com/v2/connections/072ae271620e56c4b/8183/0a84da06-3fca-4777-b257-077ffb38d661/notifications",
"contactProtocol": "HTTP Post",
"messageTypes": [
"US_NOTIFICATION_MAINTENANCE"
// all message types this connection is subscribed to
],
"spaceIndependentMessageTypes": [],
"spaceIds": [
"45d58365-547f-4b45-ab5b-53ed14cc79ed"
],
"stagingSpaceId": "00000000-0000-0000-0000-000000000000",
"ubiLocaleCode": ""
},
// .. and many more
]
}It seems to return a contactUrl for each connection for ANY user passed into it! Sending a request to this mysterious URL (with the same Ubi-headers I’ve used everywhere else) returns a simple error message telling us Error message: No notification type specified. Not knowing about the payload, I kept it in my workspace and moved on.
One day, while scrolling through Twitter, I found a interesting tweet releasing a python script, which opened the statistics of any user you blocked ingame. This was especially useful, as you couldn’t easily find the username of some players because of Siege’s streamer mode, which essentially lets you change your username with the Appear as nickname feature.
You could still click on another person in the leaderboard and either add them as a friend or add them to your blocked list.
The script simply logged into your ubisoft account, connected to the WebSocket server at wss://public-ws-ubiservices.ubi.com/v2/websocket and subscribed to the BLOCKLIST_ADD event, then proceeded to open https://r6.tracker.network/r6siege/profile/ubi/adfdcbbb-0837-4ba4-956d-36942013374d (with the UUID replaced), a third-party tracker, in a browser.
This is how messages from Ubisoft’s websocket look like:
{
"content": {
"partyId": "91bd1004-e79e-42fc-a29e-8d810df8763f",
"groupId": "119cc4c5-9b64-45ab-b1ab-27d20cc1685b",
"profileId": "8d6f1e7d-ed7b-4d13-9b07-ae62f42967f9",
"lastModifiedAt": "1970-01-01T00:00:00.001Z"
},
"notificationType": "PARTY_MEMBER_UPDATED",
"spaceId": "0d2ae42d-4c27-4cb7-af6c-2099062302bb",
"sourceApplicationId": "67312462-f1e6-4042-9a5f-370a92399d9d",
"datePosted": "1970-01-01T00:00:00.001Z"
}My brain then put two and two together and tried this exact payload on the, still mysterious, contactUrl… and proceeded to get a 200 OK.
HTTP/1.1 200 OK
Server: UbiServices Gateway /2.8.0
Content-Type: application/json; charset=utf-8
Content-Length: 2
{}I immediately got to work on getting myself banned for toxicity so I could see what the message for getting banned looked like, as I saw the space contained UPDATED_PENALTIES as a valid notification type. Sending that payload to the contactUrl also gave me a 200 OK, however nothing happened in the game. I tried a lot of other things too, however eventually I sort of gave up again.
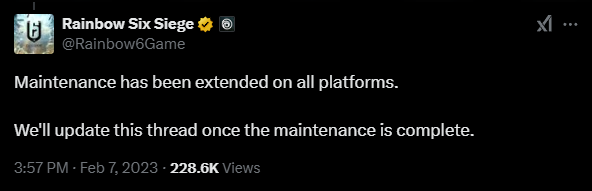
Tracking pays off
Remember how I said I wrote a small script monitoring Ubisoft’s changes to about 5 endpoints? While waiting for Ubisoft to finish their update to version Y7S4.2.0.1 on the 7th of February 2023 yes, this entire story is about 2 years old.. I’m lazy okay, they changed an interesting value in the space’s parameters:
"r6-publicConfigs": {
"fields": {
+ "PlayerNotifications.ValidAppIds": [
+ "70844177-0d2f-4120-a455-81e0f3188ead"
+ ],
"PlayerNotifications.ValidTypes": [
"UBICONNECT_VISUAL_NOTIFICATION"
],This immediately caught my eye and made me try sending the ban payload again with that specific application id… well, as soon as the maintenance ended. It was a long maintenance.
And well, it worked. I got the ban message. I sadly don’t have any screenshots anymore, this entire story is 2 years old, sorry :(
The only logical thing, at least for my 2 year younger self, I’d like to think that I’ve improved since then was to try it on Twitch streamers and other players.
See the reaction of a fairly large Siege content creator (BikiniBodhi) here:
After I, very responsibly (/s, i’m sorry), reported this issue to BikiniBodhi by disclosing the details of the exploit using the live esports ticker in the lobby, Ubisoft fixed it relatively quickly. I wonder why.
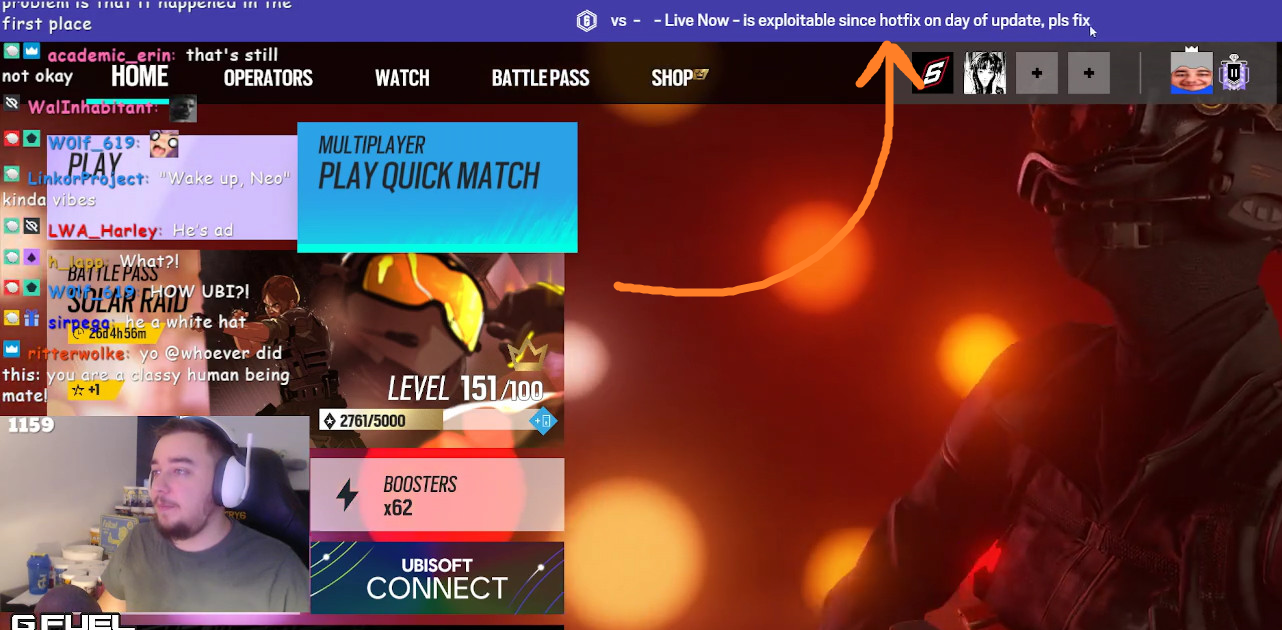
(There were many more messages from me, however I couldn’t find any clip from back then and I don’t think I have any recording of this event)
I think I got lucky finding the payload of this esports event, because there was actually an esports event going on at that time. I didn’t actually intend on catching this.
The fix
The mysterious contactUrl endpoint now checks the notificationType specified and rejects it if it “is not configured for this endpoint.”
{
"errorCode": 1030,
"errorContext": "IM",
"httpCode": 403,
"message": "Error message: Notification type UPDATED_PENALTIES is not configured for this endpoint.",
"moreInfo": "A link to more information will be coming soon. Please contact UbiServices for more support."
}What I could’ve done better
Responsible disclosure is actually really important. I disclosed this in a, well, not so good way. I only later found out that Ubisoft had a vulnerability disclosure program over at Intigriti and I probably should’ve done more research before abusing this exploit in a, kind of, funny way. At least BikiniBodhi thought it was funny.
If you have any questions, please feel free to reach out.